Blog entry by Bob Gilmore
Since the news broke of the vulnerability in OpenSSLs implementation of the Heartbeat protocols, dubbed Heart Bleed, a lot of websites have been scrambling to get patches installed.For the most part, this is proceeding quickly and successfully, at least for the big sites.
OpenSSL is the open source SSL/TSL implementation used by, basically, everybody to secure communications between server and client computers; Websites, Instant Messaging, VPNs, wait staff in restaurants, you name it. The bug appears to have been introduced in 2011 and has been known about since 2012, at least in the wild, which means a lot of people could potentially have been affected.
The bug which exposes a small 64KB chunk of memory in the client or server which can, if the attacker is lucky, expose just about any secured information; passwords, credit cards, security keys, etc.
Here is the official announcement: https://heartbleed.com/. Laughably, that the page is secured by a certificate that is not issued by a major security provider, so the page generates a certificate error when visited.
Slashdot, as usual, provides a good summary and lots of link: http://it.slashdot.org/story/14/04/09/235217/heartbleed-openssl-vulnerability-a-technical-remediation
However, this blog post is not about all the official news. It's about how it can affect a regular consumer:
- Almost all home (A)DSL routers are based on one version or another of the Linux kernel.
- They almost all implement some form of remote administration so support staff can access your router if there are any problems.
- This remote administration is often enabled by default if your router was supplied by your Internet Service Provider.
- The remote administration almost certainly uses OpenSSL for security, although you can't easily find out.
- If your router was manufactured after mid 2011, or has had a firmware update since then, it is very likely it will have this bug.
- If you have ever used the Internet to enter a password, credit card number or other detail, it is possible that you could be at risk.
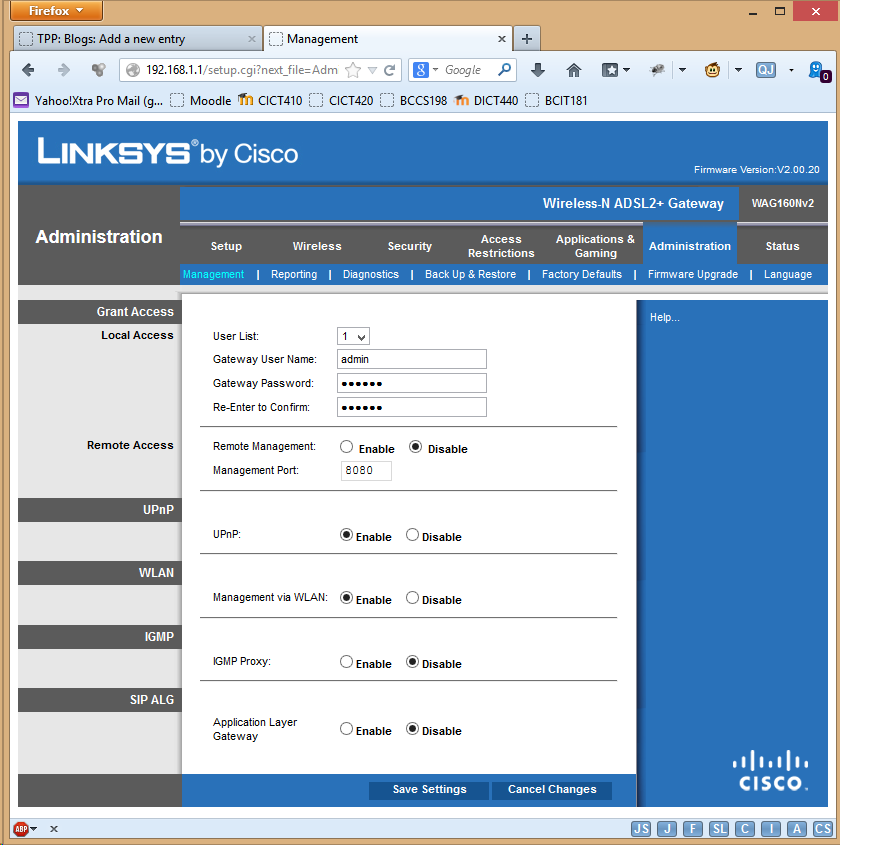
Disable your ADSL routers remote access.
Without wanting to stir up any more concern, this is a potentially serious risk and one that is going to be with us for a very long time because the manufacturers of these devices are notoriously slow to provide software updates to them, especially if they are no longer sold.
So, my advice to any user of broadband internet: find the remote administration of your ADSL router and disable it.